
Security Testing involves evaluating an application’s or system’s defenses against cyber threats. This process includes identifying vulnerabilities, weaknesses, and potential exploits to ensure robust security. Techniques such as penetration testing, vulnerability scanning, and risk assessment are employed to uncover security flaws. By doing so, organizations can enhance their defenses, protect sensitive data, and mitigate the risk of cyber attacks. Security Testing is crucial for maintaining the integrity, confidentiality, and availability of information systems in today’s digital landscape.
1. What does “vulnerability” mean?
Ans:
A fault or weakness is referred to as a vulnerability in a system’s design, implementation, or configuration that could be exploited to compromise its security. It exposes the system to potential threats such as unauthorized access, data breaches, or service disruptions. Vulnerabilities can arise from coding errors, misconfigurations, or outdated software. Regular vulnerability assessments help identify and mitigate these weaknesses.
2. Explain impromptu Testing.
Ans:
Impromptu Testing involves spontaneous and unplanned testing activities conducted without predefined test cases. Testers improvise test scenarios on the fly to explore system behavior in real-time. It aims to uncover unexpected defects and validate system usability under ad hoc conditions. Typically used during exploratory testing phases, it relies on the tester’s expertise and creativity. Documentation may be limited, focusing more on immediate feedback and rapid defect detection.
3. Explain Intrusion Detection.
Ans:
- Intrusion Detection is a security mechanism designed to monitor and detect unauthorized access or malicious activities within a network or system.
- It analyzes network traffic, system logs, and behavior patterns to identify suspicious activities.
- Intrusion Detection Systems (IDS) can be network-based, host-based, or hybrid.
- They generate alerts or take preventive actions upon detecting potential threats or anomalies.
4. What is loop testing, and how does it work?
Ans:
- Loop testing focuses on testing the functionality and behavior of loops within software code.
- It aims to validate loop constructs for correctness, efficiency, and reliability.
- Test cases are designed to exercise different loop conditions, including boundary values and typical scenarios.
- Loop testing helps identify defects related to loop initialization, execution, and termination conditions.
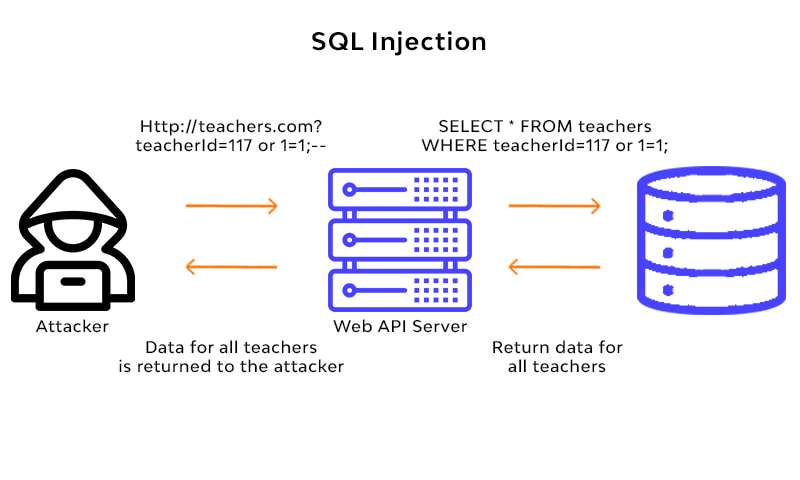
5. Explain SQL Injection.
Ans:
One kind of online attack is SQL Injection. in which malicious SQL queries are injected into the input fields of a web application. Attackers exploit vulnerabilities in poorly sanitized input to manipulate the database, which can lead to unauthorized data retrieval, modification, or deletion. Preventive measures include input validation, parameterized queries, and escaping special characters. SQL Injection attacks can be mitigated by enforcing least privilege principles and regular security audits.
6. How are security tests conducted?
Ans:
Security tests are conducted by systematically evaluating software or system components to identify vulnerabilities and validate security controls. They use methods like vulnerability assessments, penetration testing, scanning, and security code reviews. Test scenarios simulate real-world attack vectors to assess system resilience against threats. Testers analyze results to prioritize and address security risks effectively. Collaboration with security experts and adherence to industry standards enhance test accuracy and coverage.
7. What distinguishes structured Testing from unstructured Testing in particular?
Ans:
- Structured Testing follows predefined test plans, scripts, and procedures to validate specific functionalities or requirements.
- It emphasizes repeatability, traceability, and thorough documentation of test outcomes.
- In contrast, unstructured Testing involves exploratory or ad-hoc Testing without predefined test cases.
- Testers rely on intuition and experience to uncover defects and evaluate system behavior dynamically.
8. What are the qualities of security testing?
Ans:
Security testing guarantees the privacy, availability, and integrity of information systems. It identifies vulnerabilities, assesses risks, and validates security controls. Qualities include thoroughness, accuracy, and adherence to industry standards. Security testing promotes proactive detection and mitigation of security threats. It integrates with the software development lifecycle to enforce secure coding practices. Regular updates and collaboration with security experts enhance the effectiveness of security testing efforts.
9. Explain SSL. Enumerate its components.
Ans:
A cryptographic protocol called SSL (Secure Sockets Layer) makes sure that online communication is secure.
Components include:
- Encryption: Secures data transmission by converting plaintext into ciphertext.
- Authentication: Confirms the correspondence parties’identities.
- Integrity: Ensures data remains unchanged during transmission.
10. Explain the difference between black-box testing and white-box testing.
Ans:
| Aspect | Black-Box Testing | White-Box Testing |
|---|---|---|
| Definition | Complete Testing without knowledge of the internal code or structure. | Testing with knowledge of the internal code and structure. |
| Focus | Functional aspects of the application. | Internal workings and logic of the application. |
| Tester’s Knowledge | No knowledge of internal code required. | Requires knowledge of the internal code. |
| Test Basis | Based on requirements and specifications. | Based on code structure, logic, and implementation. |
11. Why does sandwich testing necessitate software testing?
Ans:
Sandwich testing ensures that the software functions correctly when integrated with other modules. It validates the interactions between modules to detect integration issues early. By testing software in integrated layers, it reduces the risk of defects in complex systems. This approach verifies that individual components work together seamlessly. It enhances overall software quality and reliability before deployment. Sandwich testing helps prevent integration-related bugs from reaching production environments.
12. What are the two most often used techniques for password file security?
Ans:
Encryption and hashing are widely used techniques for securing password files. Encryption converts passwords into ciphertext, which requires a key to decrypt. Hashing transforms passwords into irreversible hash values stored in the file. Salted hashing adds a random salt to each password before hashing to enhance security. These techniques protect passwords from unauthorized access and ensure data confidentiality. Implementing strong encryption and hashing algorithms is crucial for robust password file security.
13. What is NIDS specifically?
Ans:
- Network Intrusion Detection System (NIDS) monitors network traffic for suspicious activities or attacks.
- It analyzes packets in real time to detect unauthorized access attempts or anomalies.
- NIDS identifies potential threats based on predefined rules or anomaly detection algorithms.
- It provides alerts or triggers actions when malicious activities are detected.
- NIDS enhances network security by continuously monitoring and analyzing network traffic.
14. Describe system testing as it relates to software testing.
Ans:
- System testing verifies the behavior of a complete, integrated software system.
- It tests the system against its functional and non-functional requirements.
- System testing ensures that all components work together as expected.
- Test scenarios cover end-to-end processes to validate system functionality.
- It identifies defects in system behavior, performance, and usability.
15. Describe the advantages of pilot testing for us.
Ans:
Pilot testing allows real-world validation of software in a controlled environment. It gathers feedback from actual users to identify usability issues and improvements. Pilot tests uncover operational challenges and performance issues early in the deployment phase. This approach mitigates risks by testing software in a limited user group before full rollout. It builds user confidence and acceptance through early engagement and feedback incorporation.
16. Explain what port scanning is.
Ans:
Port scanning is a method for finding open ports on a computer or network device. It entails sending requests to target ports to determine their status and services. Port scanners detect listening services and their associated protocols (e.g., HTTP, FTP). Attackers use port scanning to identify potential vulnerabilities for exploitation. Defensive port scanning helps network administrators assess and secure their systems. Understanding port scanning helps monitor and protect network assets effectively.
17. Describe a few of the drawbacks of soak testing.
Ans:
- Soak Testing requires extended periods to adequately simulate real-world usage scenarios.
- It consumes significant resources, including time, hardware, and personnel.
- Identifying performance degradation or memory leaks may be challenging.
- Automated tools are essential but may only capture some system behavior nuances.
- Soak testing results may vary depending on environmental conditions and data loads.
18. What is the method that system testing offers?
Ans:
- System testing provides a comprehensive evaluation of software functionality and performance.
- It verifies that the entire system meets specified requirements and user expectations.
- Test cases cover integration scenarios, user interactions, and system behavior under various conditions.
- System testing ensures software reliability, scalability, and compatibility with the environment.
19. What makes software testing so vital that it includes module testing?
Ans:
Module testing validates the functionality of individual software modules or components. It detects defects early in the development lifecycle, reducing costs and risks. Testing modules independently ensure they perform as expected before integration. Identifying and fixing module-specific issues prevents broader system failures. Module testing improves software quality by addressing component-level bugs promptly.
20. List the three methods for security testing.
Ans:
Penetration testing simulates attacks to identify vulnerabilities in software or networks. Vulnerability assessment scans systems to detect potential weaknesses and security gaps. Security code review examines source code for security flaws and adherence to best practices. These methods complement each other to ensure comprehensive security testing coverage. Effective security testing enhances resilience against cyber threats and protects sensitive data.
21. What is regression testing, and why is it important?
Ans:
- Rerunning tests is a practice known as regression testing. It involves Testing previously developed and tested software to ensure that changes or additions have not adversely affected existing functionality.
- It is crucial because software evolves over time with updates and new features. Testing for regression makes sure that these modifications don’t introduce new defects or break existing functionality, maintaining overall software quality and stability.
22. What exactly are cookies, and which kinds are available?
Ans:
Small text files called cookies are kept on users’ computers and devices by websites they visit to enhance the browsing experience and track user behavior.
Types of cookies include:
- Session cookies: Temporarily stored and deleted when the browser session ends.
- Cookies that last: Stay on the gadget for a specified period, facilitating user preferences and login sessions.
23. What are the advantages of automated Testing over manual Testing?
Ans:
Compared to manual Testing, automated Testing has several advantages. The results include increased efficiency and speed in test execution, repeatability of tests with consistent results, increased test coverage, and test performance capability that could be more practical or achievable to perform manually. It reduces human error, frees up testers for more creative and exploratory testing tasks, and supports continuous integration and delivery pipelines by providing fast feedback on code changes.
24. Describe the concept of boundary value analysis in Testing.
Ans:
Analyzing boundary values is a technique for Testing that concentrates on boundary values of input ranges rather than testing every possible input value. It is to uncover errors at boundaries or limits of input values, where software behavior may change. By testing values at the edges of valid and invalid ranges, boundary value analysis helps ensure the robustness and accuracy of the software, identifying potential off-by-one errors or boundary-related issues that might affect functionality or performance.
25. How does stress testing differ from load testing?
Ans:
- Stress testing evaluates the software’s behavior under extreme conditions, such as maximum load, limited resources, or peak usage periods, to determine its robustness and reliability under stress.
- It aims to identify breaking points or failure thresholds.
- Load testing, on the other hand, assesses the software’s performance under expected or anticipated normal conditions of use, measuring its response times, throughput, and resource utilization.
- Both tests aim to ensure that the software meets performance expectations but focus on different aspects of scalability and resilience.
26. What are the fundamental principles of agile Testing?
Ans:
- Agile testing principles emphasize continuous Testing throughout the development lifecycle, collaboration between developers and testers, early and frequent feedback, and adapting testing processes to changing requirements.
- Testing is integrated into every phase of agile development, with a focus on delivering working software increments and responding to changes quickly.
- Agile Testing prioritizes customer satisfaction and flexibility and delivers business value through iterative development and testing cycles.
27. Explain the concept of test-driven development (TDD).
Ans:
Software development using test-driven development (TDD) involves writing tests before writing any code. Dev lopers write automated tests that define the desired functionality, run these tests (which initially fail as no code exists), and then write the minimum code required to pass the tests. TDD promotes straightforward, modular code design, ensures comprehensive test coverage, and supports code refactoring with confidence.
28. What is the purpose of usability testing in software development?
Ans:
Usability testing evaluates how user-friendly and intuitive a software application is by observing real users interacting with it. It identifies usability issues, such as confusing navigation, unclear instructions, or inefficient workflows, that could hinder user experience and satisfaction. By gathering feedback from representative users early in the development process, usability testing helps improve design decisions, prioritize enhancements, and ultimately deliver a more user-centric product.
29. Describe the role of a test plan in software testing.
Ans:
- A test plan outlines the approach, objectives, scope, and materials needed for testing a software application or system.
- It serves as a roadmap that guides testing activities, including test design, execution, and evaluation, to ensure comprehensive coverage of requirements and quality goals.
- The test plan defines test objectives, test strategies, entry and exit criteria, test environments, schedules, and responsibilities.
- It provides a basis for communication among stakeholders, manages expectations, and ensures that testing activities align with project goals and constraints.
30. How does smoke testing differ from sanity testing?
Ans:
- A new build is subject to a preliminary test to ensure that the software’s critical functionalities work without significant issues.
- It is usually broad and shallow, aiming to verify basic functionalities.
- Conversely, regression testing is a subset of sanity testing. It is focused on checking specific areas of functionality after a minor change or bug fix to ensure that the most recent modifications haven’t negatively impacted related functionalities.
- It is narrower in scope compared to smoke testing and verifies specific aspects or fixes.
31. What are the different levels of Testing typically carried out in a software project?
Ans:
In a software project, Testing occurs at multiple levels: Unit Testing focuses on individual components to ensure they function as intended. Integration Testing checks interactions between integrated units to verify they work together correctly. Sys em Testing validates the entire system against requirements to ensure it meets user expectations. Acceptance Testing is performed to gain user acceptance and confirm business requirements. Reg session Testing ensures that changes do not unintentionally affect existing functionalities.
32. Explain the concept of acceptance testing. How is it different from system testing?
Ans:
Acceptance Testing verifies if a system meets business requirements and user expectations before deployment. It often involves end-users or stakeholders validating functionality in a real-world scenario. System Testing, on the other hand, focuses on verifying the entire system’s functionality against predefined specifications and design documents. Both ensure software quality and acceptance testing validates user acceptance and business requirements directly, whereas system testing checks technical and functional requirements comprehensively.
33. What are the common types of software defects encountered during Testing?
Ans:
Common software defects include Functional Defects, where the software does not perform as intended; Performance Defects, which impact system responsiveness or efficiency; Compatibility Defects, affecting software operation across different platforms or environments; Usability Defects, hindering user interaction or experience; Security Defects, exposing vulnerabilities to unauthorized access; and Interface Defects, disrupting interactions between system components or external interfaces.
34. Describe the importance of the traceability matrix in software testing.
Ans:
- A traceability matrix links requirements to test cases, ensuring that each requirement has corresponding tests and that each test case validates specific requirements.
- It helps in comprehensive test coverage, ensuring all aspects of the software are tested.
- Additionally, it aids in managing change impact analysis by identifying which tests are affected when requirements change.
- This traceability improves accountability and transparency across the testing process, facilitating easier auditing and compliance with regulatory standards.
35. What is the role of a defect-tracking system in software testing?
Ans:
- A defect-tracking system records and manages issues or bugs identified during the testing and development phases.
- It tracks each defect from discovery through resolution, providing visibility into defect status, priority, and assignment.
- This system facilitates effective communication among team members by centralizing defect information and allowing collaboration on resolutions.
- It also enables trend analysis to identify recurring issues and supports continuous improvement efforts by prioritizing fixes based on severity and impact on software quality.
36. Explain the concept of exploratory Testing.
Ans:
Exploratory Testing is a dynamic, unscripted approach in which testers simultaneously design and execute tests. It relies on the tester’s domain knowledge and intuition to uncover defects, emphasizing real-world user scenarios. Unlike scripted Testing, exploratory Testing encourages creativity and adaptability, allowing testers to explore diverse paths and interactions. This method is beneficial for discovering unexpected issues, verifying usability, and enhancing test coverage in complex or evolving systems.
37. How is risk-based Testing conducted? Provide an example.
Ans:
In risk-based Testing, testing efforts are prioritized according to recognized hazards to the project or system. Test cases are designed and executed to mitigate the highest-priority dangers first. For example, in an e-commerce application, a high-risk scenario might involve payment processing failure, leading to financial losses and customer dissatisfaction. Testing efforts would focus on thoroughly validating payment transactions and error-handling mechanisms to mitigate this risk before less critical functionalities.
38. What are the benefits of continuous integration in the context of software testing?
Ans:
- Continuous Integration (CI) automates the process of merging code updates that are stored in a common repository, which starts tests and builds automatically.
- This ensures early detection of integration issues, reducing the likelihood of costly defects in later stages.
- CI promotes faster feedback loops, enabling developers to address issues promptly and maintain software quality.
- It enhances collaboration by providing visibility into build and test results, fostering a culture of continuous improvement and reliable software delivery.
39. Describe the concept of code coverage in Testing.
Ans:
- The perCode coverage, compared to total code lines, measures the age of code run during Testing and measures the effectiveness of Testing by identifying untested or poorly tested areas.
- High code coverage suggests comprehensive Testing and potentially fewer undetected defects. However, it does not guarantee defect-free software, as it focuses on test execution rather than test effectiveness.
- Various types include statement coverage, branch coverage, and path coverage, each offering insights into different aspects of test coverage.
40. What is meant by the term “scalability testing”?
Ans:
Scalability testing evaluates a system’s ability to handle growing amounts of users, transactions, or data without compromising performance or functionality. It assesses how well the system scales up or down under varying loads and resources. This Testing is crucial for applications expected to accommodate increasing user demands over time. By imitating scenarios of increased usage, scalability testing identifies performance bottlenecks, resource limitations, and scalability issues early in the development lifecycle, ensuring robust and scalable software solutions.
41. Explain the concept of performance profiling in software testing.
Ans:
Performance profiling involves analyzing a software system’s execution to identify bottlenecks and optimize performance. It measures CPU usage, memory consumption, and I/O operations during runtime. By identifying inefficient code or resource-intensive operations, profiling helps developers improve application speed and efficiency, enhancing user experience and scalability.
42. How is security testing integrated into the software development lifecycle (SDLC)?
Ans:
- Security testing is integrated throughout the SDLC to identify and mitigate vulnerabilities early.
- Security requirements are defined in the planning phase. Sec re-coding practices are enforced during development, and static analysis tools are used.
- Testing phases include vulnerability assessments and penetration testing. Post-release, continuous monitoring ensures ongoing security.
- This integration ensures that security concerns are addressed proactively at each stage, reducing risks and enhancing overall software security.
43. Describe the difference between vulnerability assessment and penetration testing.
Ans:
- Vulnerability assessment identifies and quantifies vulnerabilities in a system, typically through automated scans and checks.
- It provides a broad view of potential weaknesses but does not exploit them.
- Conversely, penetration testing entails mimicking actual attacks to exploit vulnerabilities and assess the system’s resistance to them.
- It provides a deeper understanding of security gaps through manual testing techniques and helps prioritize remediation efforts.
44. What are some common security threats that penetration testing aims to identify?
Ans:
Penetration testing aims to uncover vulnerabilities such as SQL injection, cross-site scripting (XSS), authentication flaws, and misconfigurations. It also targets weaknesses in network security, including insecure protocols and inadequate access controls. By identifying these threats, penetration testing helps organizations fortify their defenses against potential exploits and data breaches.
45. How does fuzz testing contribute to software security?
Ans:
Fuzz testing involves injecting invalid or unexpected inputs into a software application to identify vulnerabilities like buffer overflows or crashes. By subjecting the software to various malformed inputs, fuzz testing helps uncover unknown vulnerabilities that attackers might exploit. It complements other testing methods by focusing on unexpected behaviors, enhancing overall software resilience and security.
46. Explain the concept of OWASP Top 10 in web application security.
Ans:
- OWASP Top 10 lists the most critical security risks faced by web applications, based on community consensus.
- It includes vulnerabilities like injection flaws, broken authentication, sensitive data exposure, and security misconfigurations.
- By focusing on these top risks, developers can prioritize mitigation efforts and adopt best practices to secure their web applications against common threats.
47. Describe the importance of data integrity testing in database applications.
Ans:
- Data integrity testing ensures that data remains accurate, consistent, and reliable throughout its lifecycle within a database.
- It verifies that data operations, such as insertions, updates, and deletions, maintain referential integrity and constraints.
- Data integrity testing helps maintain data quality, compliance with business rules, and overall application reliability by detecting anomalies or corruption early.
48. What role does configuration testing play in software deployments?
Ans:
Configuration testing validates that software applications perform correctly under different configurations, such as operating systems, browsers, or network settings. It ensures compatibility and functionality across diverse environments, reducing deployment risks and user experience issues. By systematically testing configurations, organizations can guarantee consistent performance and reliability across varied deployment scenarios.
49. How are test cases prioritized during the testing phases?
Ans:
Test case prioritization involves ranking tests based on factors like criticality, risk impact, and dependencies. High-priority tests address core functionalities or critical paths, ensuring essential features are thoroughly validated first. Devencies between test cases influence sequencing to avoid bottlenecks. Price mitigation strategies adapt throughout testing phases to maximize coverage and efficiency, focusing on mitigating the highest-risk scenarios early.
50. Describe the concept of static Testing in software development.
Ans:
- Static Testing examines software artifacts, such as code or documentation, without executing them.
- It identifies defects, inconsistencies, or violations of coding standards through reviews, inspections, or automated tools.
- By detecting issues early in the development lifecycle, static Testing enhances code quality, reduces debugging efforts, and fosters collaborative improvement.
- It complements dynamic Testing by addressing structural flaws and improving overall software reliability.
51. What is the purpose of a test harness in Automated Testing?
Ans:
- A test harness automates the execution and evaluation of test cases, providing a controlled environment for Testing.
- It integrates test scripts with the system under test, facilitating repeatable and reliable testing processes.
- Managing test data and configurations ensures consistency and accuracy in testing outcomes, aiding in the identification of defects early in the development cycle.
52. Explain the concept of mutation testing in software testing.
Ans:
Mutation testing involves minor alterations (mutations) to the source code to evaluate whether existing test cases can detect these changes. By intentionally introducing minor bugs or modifications, the effectiveness of the test suite is assessed by measuring its ability to identify and respond to altered code behavior. This technique plays a crucial role in improving the quality of test cases, as it reveals gaps in test coverage, highlights weaknesses in the testing process, and ensures that the test suite is robust enough to catch unexpected code changes or errors.
53. How does usability testing differ from accessibility testing?
Ans:
Usability testing evaluates how user-friendly and intuitive a software application is for its intended users, focusing on ease of use and efficiency. Accessibility testing, on the other hand, ensures that the application can be accessed and used by individuals with disabilities, adhering to accessibility standards like WCAG. While usability testing targets general user experience, accessibility testing specifically addresses inclusivity and compliance with accessibility guidelines.
54. Describe the role of a test environment in software testing.
Ans:
- A test environment replicates the production environment where software testing takes place without affecting live systems.
- It provides a controlled setting to execute test cases, validate functionality, and assess performance under simulated conditions.
- The test environment includes necessary hardware, software, configurations, and test data, ensuring that Testing is conducted in an isolated and realistic environment before deployment.
55. What are the key metrics used to measure the effectiveness of software testing?
Ans:
- Test coverage (percentage of code covered by tests).
- Defect detection rate (number of defects found per test phase).
- Test execution efficiency (time taken to execute tests).
- Regression test effectiveness (ability to uncover regressions).
These metrics help gauge the thoroughness, efficiency, and reliability of testing efforts, aiding in continuous improvement and ensuring software quality.
56. How can exploratory Testing complement scripted testing approaches?
Ans:
Exploratory Testing involves simultaneous learning, test design, and test execution based on tester intuition and domain knowledge. It complements scripted Testing by uncovering unexpected defects and scenarios that scripted tests may miss. Its adaptive nature allows testers to explore complex functionalities and edge cases dynamically, enhancing test coverage and overall software quality assurance.
57. Explain the concept of API testing and its significance in modern software development.
Ans:
- Application programming interfaces (APIs) are tested for usefulness, dependability, performance, and security.
- It ensures seamless communication between software components and integration with external systems.
- API testing is crucial in modern software development. It verifies data exchange, error handling, and adherence to API specifications, facilitating robust and interoperable applications.
58. What are some common challenges faced in Automated Testing? How can they be mitigated?
Ans:
- Challenges include initial setup complexity, maintenance overhead, and inadequate test coverage.
- Mitigation strategies involve selecting appropriate tools and frameworks, establishing clear automation goals, prioritizing test cases based on risk, and regular maintenance of test scripts.
- Collaboration between development and testing teams, along with continuous evaluation and adaptation of automation strategies, helps address these challenges effectively.
59. Describe the concept of continuous Testing in DevOps practices.
Ans:
Continuous Testing integrates automated Testing throughout the software delivery pipeline in DevOps, ensuring that each code change is validated instantly. It provides fast feedback on quality, detects defects early, and maintains application stability. Continuous Testing supports continuous integration and deployment by automating regression, integration, and performance tests, enabling faster delivery of high-quality software.
60. How does localization testing differ from internationalization testing?
Ans:
Localization testing verifies whether a software application adapts to specific regional or cultural requirements, such as language, currency, date formats, and legal requirements. Testing for internationalization ensures that code changes are not necessary for the product to be readily translated into other languages and locales. While internationalization prepares the software for global markets, localization ensures it meets local user expectations and regulatory standards.
61. What are the key characteristics of a good test case?
Ans:
A good test case is detailed and precise, outlining specific inputs, expected outcomes, and clear steps for execution. It should be self-contained, ensuring it can run independently of other test cases, which enhances its reliability and ease of use. Reusability is critical, allowing the test case to be applicable across various scenarios and saving time and effort in future testing. Measurable success criteria are essential, providing clear indicators of whether the test has passed or failed.
62. Describe the concept of load balancing and its impact on Testing.
Ans:
- Load balancing refers to distributing incoming network traffic across multiple servers to optimize resource utilization, maximize throughput, and minimize response time.
- In Testing, load balancing impacts performance testing by simulating realistic user loads to assess system scalability and reliability under varying conditions, ensuring it can handle expected user traffic efficiently.
63. How does compatibility testing contribute to software quality assurance?
Ans:
- Compatibility testing ensures that software functions correctly across different environments, devices, browsers, and operating systems.
- By validating compatibility, QA teams ensure a consistent user experience and functionality, reducing compatibility-related issues post-release.
- It enhances software quality by addressing potential usability, performance, and integration challenges early in the development lifecycle.
64. Explain the concept of reliability testing in software engineering.
Ans:
Reliability testing is a critical process that evaluates a system’s ability to perform consistently and dependably over an extended period under specific conditions. This type of testing subjects the software to varying stress levels, including peak loads, prolonged usage, and unexpected disruptions, to uncover potential points of failure. By identifying weaknesses and testing recovery mechanisms, reliability testing aims to enhance the software’s stability, ensuring it remains functional and responsive even under adverse conditions.
65. What role does a test management tool play in software testing?
Ans:
A test management tool organizes test cases, manages test execution, tracks defects, and generates reports to streamline the testing process. It neutralizes testing activities, facilitates collaboration among team members, and provides visibility into testing progress and results. This tool enhances efficiency, ensures test coverage, and supports decision-making throughout the software development lifecycle.
66. Describe the difference between validation and verification in the context of software testing.
Ans:
- Verification ensures that the software adheres to its specifications and requirements, confirming whether it was built correctly.
- Validation, on the other hand, verifies whether the software meets the customer’s expectations and needs, ensuring it effectively solves the right problem.
- Together, verification and validation ensure software quality and alignment with both technical and user requirements.
67. How is integration testing different from unit testing?
Ans:
- Integration testing validates interactions between integrated components or modules to ensure they work together as expected.
- It focuses on testing interfaces, data flow, and interaction scenarios.
- Unit testing, in contrast, tests individual units or components in isolation to verify their correctness.
- Integration testing occurs after unit testing and ensures cohesive system functionality beyond individual units.
68. What are the benefits of using mock objects in unit testing?
Ans:
Mock objects simulate the behavior of natural objects, enabling isolated Testing of components without dependencies. They enhance test reliability by providing controlled responses, facilitating Testing of error handling and edge cases, and speeding up test execution. Mock objects also support parallel development and integration testing by replacing complex dependencies with predictable and manageable substitutes.
69. Explain the concept of behavioral-driven development (BDD) and its relation to Testing.
Ans:
BDD focuses on collaborative interactions between developers, QA, and business stakeholders to define behavior through examples using structured scenarios or user stories. It emphasizes business outcomes over technical implementation, using natural language specifications (like Gherkin) to automate acceptance criteria Testing. BDD aligns testing with business objectives, improves communication, and ensures software meets desired behavior.
70. How is test automation implemented in continuous delivery pipelines?
Ans:
- In continuous delivery pipelines, test automation involves integrating automated tests at various stages (unit, integration, acceptance) to validate changes rapidly and consistently.
- Automated tests are triggered automatically upon code changes, ensuring quick feedback loops.
- This automation accelerates delivery, enhances quality by detecting defects early, and supports continuous integration and deployment practices effectively.
71. Describe the concept of non-functional Testing and provide examples.
Ans:
- Non-functional Testing evaluates aspects of a system beyond its functionality, focusing on performance, reliability, usability, and security.
- Examples include load testing to assess performance under expected load, security testing to identify vulnerabilities, and usability testing to gauge user-friendliness.
72. What are some common challenges faced in mobile app testing?
Ans:
Mobile app testing faces several challenges, including device fragmentation, where the vast array of devices, operating systems, and versions complicates ensuring consistent performance and functionality. Network conditions also pose significant challenges, as varying connection speeds and reliability can affect app performance. Ensuring compatibility across platforms, such as Android and iOS, requires extensive testing to maintain a uniform user experience.
73. How does exploratory Testing contribute to uncovering hidden defects?
Ans:
Exploratory Testing is a dynamic approach in which testers simultaneously learn, design, and execute test cases based on their intuition and experience. Unlike Scripted Testing, which follows predefined steps, exploratory Testing encourages creativity and adaptability. Testers leverage their domain knowledge to explore various scenarios and paths through the application in real-time, uncovering defects that scripted tests might miss.
74. Explain the concept of sanity testing in relation to regression testing.
Ans:
- Sanity testing is a focused validation process that ensures the core functionalities of a software application remain intact and operate correctly after minor updates or bug fixes.
- Unlike regression testing, which examines the entire application to confirm that recent changes haven’t caused unintended impacts, sanity testing targets essential features only.
- This approach is efficient, as it doesn’t require retesting all functionalities but instead concentrates on critical areas to verify stability and functionality post-change.
75. What is the purpose of performance testing tools in software development?
Ans:
Performance testing tools are essential for evaluating a system’s behavior under different conditions, such as varying loads, stress levels, and scalability scenarios. These tools help pinpoint performance bottlenecks that could degrade user experience or system efficiency. Simulating high user loads ensures that applications meet or exceed expected performance benchmarks, validating their reliability and stability under pressure.
76. Describe the importance of error handling Testing in software applications.
Ans:
Error handling testing is a critical aspect of software testing that evaluates how an application responds to unexpected inputs, errors, and exceptions. This type of Testing is essential to ensure that applications gracefully recover from faults and mistakes, preventing crashes and maintaining user trust. By dynamically injecting unexpected scenarios and erroneous inputs into the application, testers can verify its ability to handle such situations effectively.
77. How does boundary testing help in identifying software vulnerabilities?
Ans:
- Boundary testing is a critical software testing technique that evaluates how an application performs at its operational limits and just beyond.
- It focuses on testing input boundaries, such as minimum and maximum values allowed for inputs, to uncover vulnerabilities related to buffer overflows, data truncation, and unexpected behavior caused by edge conditions.
- This method ensures that the software effectively handles extreme values and edge cases, thereby enhancing its robustness and reliability.
78. What are some techniques used in a security code review?
Ans:
Techniques in security code review encompass several critical approaches to identify and mitigate vulnerabilities. Manual code inspection allows for a detailed examination of the codebase to uncover potential security flaws. At the same time, automated scanning tools detect common security issues, such as SQL injection, cross-site scripting (XSS), and other vulnerabilities. Threat modeling assesses potential risks by anticipating how an attacker might exploit the system.
79. Describe the concept of threat modeling in software security.
Ans:
Threat modeling is a structured approach that systematically identifies and evaluates potential threats and vulnerabilities within a software application. It begins with a comprehensive understanding of the application’s architecture, including its components, interfaces, and data flows. By analyzing the system from an attacker’s perspective, threat modeling defines potential attack vectors that malicious actors could exploit.
80. How is static code analysis used in identifying potential security issues?
Ans:
- Static code analysis is a crucial software testing technique that scrutinizes source code without executing it, focusing on identifying security vulnerabilities, coding errors, and potential weaknesses.
- By analyzing the code structure and logic, static analysis tools scan for known patterns and insecure coding practices that could lead to bugs or security breaches.
- This proactive approach provides developers with actionable insights early in the development cycle, allowing them to address issues promptly and enhance overall code security before deployment.
81. Explain the concept of penetration testing in cloud-based applications.
Ans:
- Penetration testing in cloud-based applications involves simulating cyberattacks to identify vulnerabilities in the cloud infrastructure, applications, or services.
- It assesses security controls and helps ensure robust defenses against potential threats.
- By testing various attack scenarios, organizations can proactively strengthen their security posture in the cloud.
82. What are the benefits of using automated security testing tools?
Ans:
Automated security testing tools offer several advantages, including faster detection of vulnerabilities, consistent testing coverage, and reduced manual effort. They enable organizations to identify security flaws early in the development cycle, improving overall software security. Automated tools also support continuous testing and integration processes, enhancing agility and reducing time to market.
83. Describe the role of compliance testing in software security.
Ans:
Software compliance testing ensures a software system adheres to company policies, industry standards, and legal requirements. This testing process evaluates whether the implemented security controls and practices align with specified criteria and effectively address legal and contractual obligations. By rigorously testing for compliance, organizations can identify potential vulnerabilities, mitigate risks, and safeguard sensitive data from breaches or misuse.
84. How does encryption testing contribute to data security?
Ans:
- Encryption testing evaluates the effectiveness of cryptographic algorithms and critical management practices in protecting data confidentiality and integrity.
- It verifies if encryption mechanisms function correctly across different scenarios and environments.
- Effective encryption testing helps prevent unauthorized access to sensitive information, ensuring robust data security.
85. Explain the concept of session management testing in web applications.
Ans:
- Session management testing assesses how web applications handle user sessions, including authentication, session creation, maintenance, and termination.
- It verifies if session tokens are securely generated, transmitted, and stored to prevent session hijacking or fixation attacks.
- Effective Testing ensures reliable session management, enhancing overall application security.
86. What are the challenges associated with performance testing of microservices architectures?
Ans:
Performance testing of microservices architectures introduces several challenges due to the intricate dependencies between individual microservices, which can complicate identifying the root causes of performance issues. The dynamic nature of microservices, which can scale up or down based on demand, adds complexity to maintaining consistent performance across distributed environments. Ensuring that each microservice performs optimally in isolation and within the broader system is essential for detecting and resolving bottlenecks.
87. How does cross-site scripting (XSS) differ from cross-site request forgery (CSRF)?
Ans:
Cross-site scripting (XSS) is a security vulnerability that occurs when an attacker injects malicious scripts into web pages that are viewed by other users. These scripts are executed in the context of the user’s browser, exploiting trust relationships within the application, and can lead to unauthorized actions, data theft, or session hijacking. In contrast, cross-site request forgery (CSRF) exploits the trust that a web application has in the user’s browser by tricking authenticated users into unknowingly executing unwanted actions on behalf of the attacker.
88. Describe the importance of database testing in software applications.
Ans:
- Database testing ensures data integrity, accuracy, and reliability within software applications.
- It validates database schema, queries, transactions, and data manipulation operations to detect errors or performance issues.
- Effective database testing mitigates risks of data corruption, security breaches, and application failures, ensuring robust application functionality.
89. What role does code review play in ensuring software quality?
Ans:
Code review is a systematic examination of source code to identify defects, improve code readability, and ensure adherence to coding standards and best practices. Facilitating collaborative evaluation enhances software quality through early detection of bugs and inconsistencies, reducing the likelihood of defects reaching later stages of development. Code reviews also promote knowledge sharing among team members, enabling them to learn from each other’s expertise and insights.
90. Explain the concept of end-to-end Testing in software development.
Ans:
End-to-end Testing validates the entire software application flow from start to finish, simulating real-world user scenarios across all system components. It ensures seamless integration and interaction between various modules, interfaces, and external dependencies. Eff active end-to-end Testing verifies functionality, performance, and reliability, addressing potential issues before deployment.
91. How can test-driven development (TDD) improve code quality and test coverage?
Ans:
- Test-driven development (TDD) improves code quality by requiring small, modular designs and thorough test coverage from the outset.
- Developers write tests before writing functional code, ensuring each feature is validated against expected behavior.
- This approach encourages precise specifications and reduces the likelihood of defects.
- TDD also enhances test coverage as it necessitates creating tests for each new code release, ensuring all edge cases and scenarios are considered.
92. Describe the concept of A/B testing and its relevance in user experience testing.
Ans:
- A/B testing involves evaluating two (A and B) versions of a website or application to see which functions better based on user engagement metrics.
- It’s crucial in user experience testing as it allows for the direct comparison of design elements, content variations, or functionalities.
- By randomly assigning users to different versions, A/B testing provides empirical data on which design or feature resonates best with users.
- This iterative process helps optimize user experience, leading to informed decisions backed by data rather than assumptions.
93. What are the benefits of using virtualization in software testing environments?
Ans:
Virtualization in software testing creates isolated, reproducible environments that mimic production setups without additional hardware costs. It allows testers to deploy multiple configurations swiftly, test on different operating systems, and simulate network conditions. Virtualization enhances testing efficiency by reducing setup time and enabling parallel Testing of applications across various environments. Furthermore, it facilitates easy snapshots and rollbacks of test environments, ensuring consistent testing conditions and minimizing disruptions.
94. How does continuous monitoring contribute to software security?
Ans:
Continuous monitoring in software security involves real-time tracking of system activities, network traffic, and application behavior to detect anomalies or potential security breaches promptly. It provides insights into system performance and identifies vulnerabilities early in the development lifecycle. By monitoring logs, metrics, and user activities continuously, organizations can respond swiftly to threats, apply patches proactively, and enforce security policies effectively.
95. Describe the concept of regression test selection and its advantages in Agile development.
Ans:
- Regression test selection involves identifying and executing only the necessary tests affected by recent changes rather than re-running all tests.
- In Agile development, where changes are frequent, this method ensures that while saving time and resources, modifications haven’t inadvertently affected existing functionality.
- By focusing on impacted areas, teams can maintain a balance between thorough Testing and rapid delivery cycles.
- Regression test selection speeds up feedback loops, allowing teams to release updates more confidently and frequently without compromising product quality.






